Key Features
Investment Justification
Test your SOC response on a real threat and demonstrate the value of IT Security investments to the Executive Board by simulating modern adversary behaviors.
On Demand Verification
Easy measurement and on-demand verification if your current network security solutions meet the compliance policy assumptions and work as expected
Red Team Automation
Out of the box adversary tools, techniques, and procedures delivered in the box allows for quickly deliver value and save time and money.
Skills Improvement
Continuous learning about details of sophisticated network data exfiltration and lateral movement actions you have not been aware of before
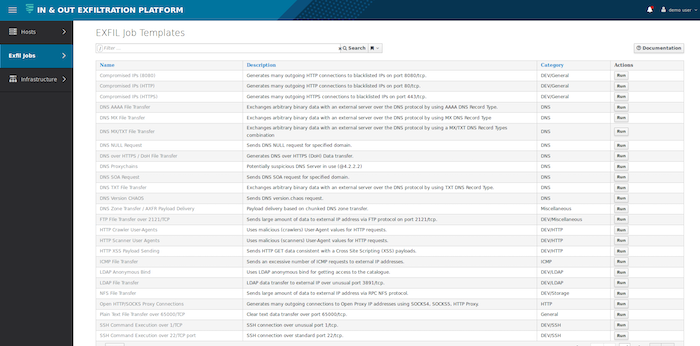
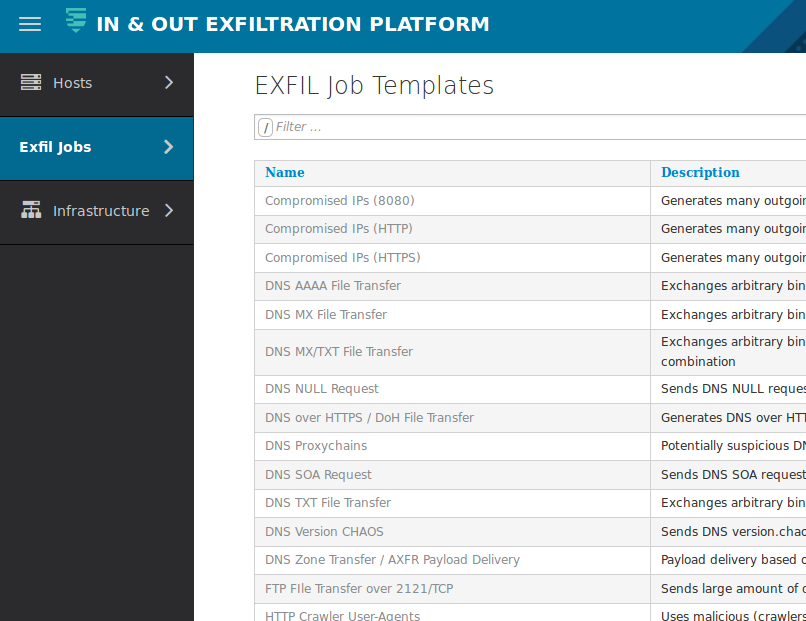
Platform
Basic Subscription
The single-node environment provided as VM image dedicated for Business:
- Ready to run on your own laptop
- One direction traffic only - internal to external
- A limited number of eXfil job definitions
- Shared C2 infrastructure
- Full access to the In & Out Knowledge Base
- Supports Proof of Concept / Proof of Value programs
- Useful for Technical Presales Engineers who want to sell better IT Security products

Enterprise Subscription
The multi-node environment provided as VM images dedicated to Enterprise:
- Ready to run in your multi-segment enterprise environment
- Multi-direction traffic (int2ext, int2dmz, dmz2ad, ad2mgmt, ad2ad, int2int, etc.)
- The full number of eXfil job definitions
- Dedicated C2 Cloud Infrastructure
- Full access to the In & Out Knowledge Base
- Useful for Red / Blue / Purple teams who want to validate network security posture
- Training and workshops included
Try for free
Sign up for a 7 days demo access. No credit card required.
What you will get:
- 7 days of Demo Access to play with the platform in the cloud
- The full list of simulation job definitions
- Cloud-based DEMO environment
- No Credit Card required
- No installation steps - just the web browser needed
Our Customers & Recommendations
Contact Us
If you have any question, please use the form below:

















