The Crucial Significance of Modern Linux Detection and DFIR
In the ever-evolving landscape of cybersecurity, the importance of Linux detection and Digital Forensics and Incident Response (DFIR) cannot be overstated. In this post, we delve into the profound significance of these aspects, particularly from a low-level understanding of Linux internals, subsystems, and the /sys and /proc paths.
- Linux is renowned for its modularity and complexity. With a plethora of subsystems, kernel modules, and low-level interfaces, understanding its internals is no small feat. Modern Linux distributions have evolved to support a wide range of hardware architectures, file systems, and device drivers. This diversity is a double-edged sword—it offers flexibility but also introduces complexities that can be exploited by malicious actors. Proper Linux detection is essential to identify vulnerabilities, anomalies, and potential security breaches within these intricate systems.
Watch for /proc/kallsyms suspicious entries: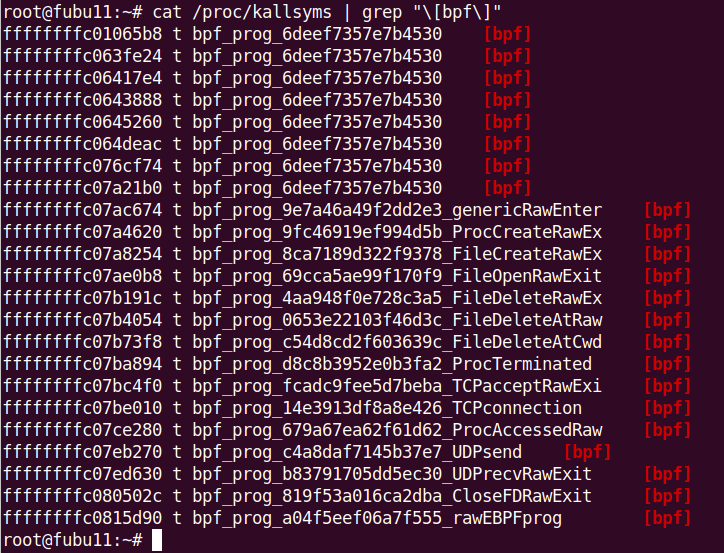
- The /proc and /sys directories are windows into the heart of the Linux kernel and are accessible through the file system. The /proc directory provides information about running processes, system parameters, and hardware configurations. Meanwhile, /sys exposes kernel parameters and device attributes. While these paths offer invaluable insights, they also serve as a potential goldmine for attackers. A robust DFIR approach is essential to monitor and investigate activities within /proc and /sys, ensuring that no unauthorized changes or malicious activities go unnoticed.
Example of Kovid rootkit behavior (ftrace-based hooking):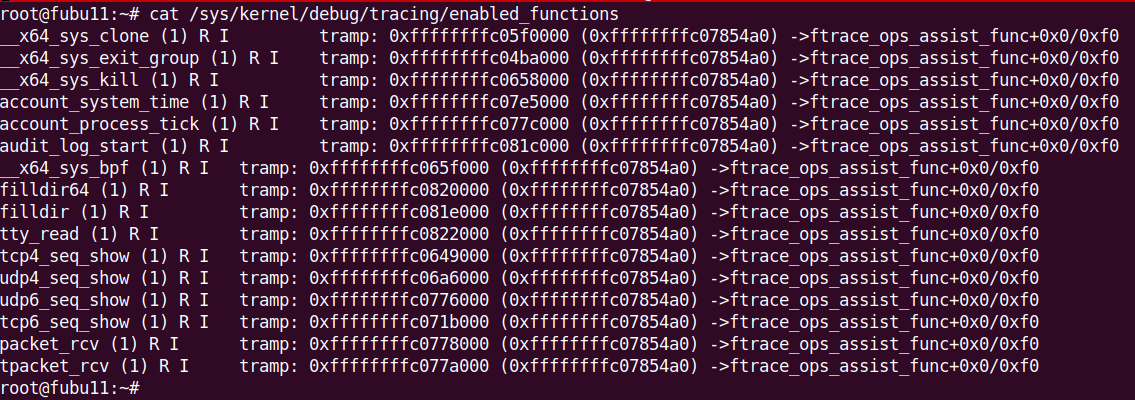
- Protection of Critical Infrastructure: Linux is a prevalent choice for critical infrastructure systems, including servers, routers, and embedded devices. These systems often run continuously and are essential for the functioning of society. Effective Linux detection and DFIR practices are indispensable for safeguarding these critical assets from cyberattacks that could have far-reaching consequences.
Tracee vs system calls hooking: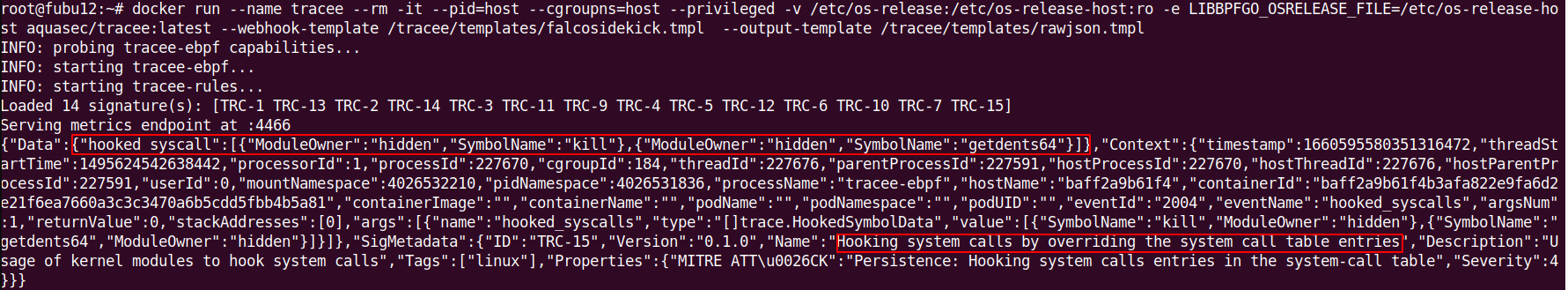
- Linux's open-source nature has fostered a vibrant community of developers, researchers, and security experts. Collaboration within this ecosystem is vital for sharing knowledge about emerging threats and best practices in DFIR. The Linux community plays a pivotal role in advancing the field of cybersecurity by constantly improving tools and techniques for detection and response.
Velociraptor Yara Scan vs Openssh-backdoor: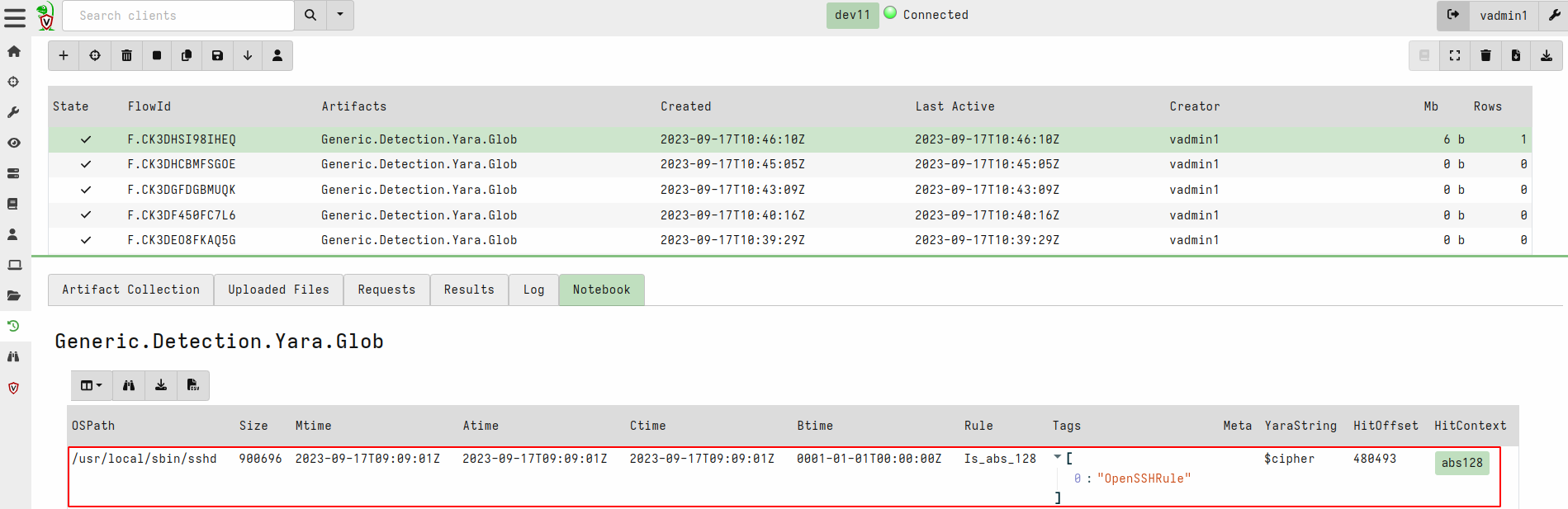
- In a world where cyber threats are continually evolving, timely detection and swift response are paramount. Modern Linux detection techniques leverage kernel-level monitoring, audit logs, and advanced heuristics to identify suspicious activities. DFIR strategies involve not only identifying potential threats but also reacting effectively to contain and mitigate them. The quicker the response, the less damage a cyber incident can cause.
LKRG vs reptile rootkit: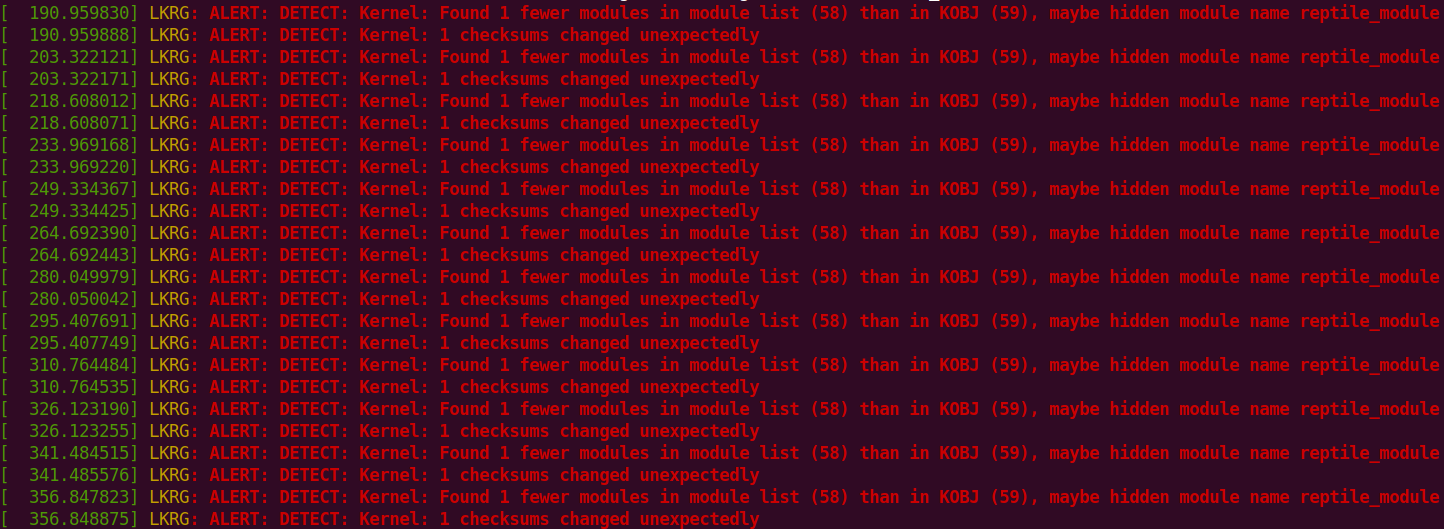
In conclusion, modern Linux detection and DFIR are not just optional components of cybersecurity; they are foundational elements for protecting today's complex and diverse computing environments. With the ever-expanding threat landscape and the intricate nature of Linux internals, the need for proactive detection and rapid incident response has never been more critical. To ensure the integrity and security of Linux systems, organizations must invest in robust detection tools, expert personnel, and a proactive DFIR strategy.
Want to learn more? Check out the "Linux Attack, Detection, and LIve Forensics" self-learning course with 90 days of PurpleLabs access and lifetime access to materials + UPDATES!