Elastic Security
Elastic Security unifies SIEM, endpoint security, and cloud security on an open platform, arming SecOps teams to protect, detect, and respond at scale.
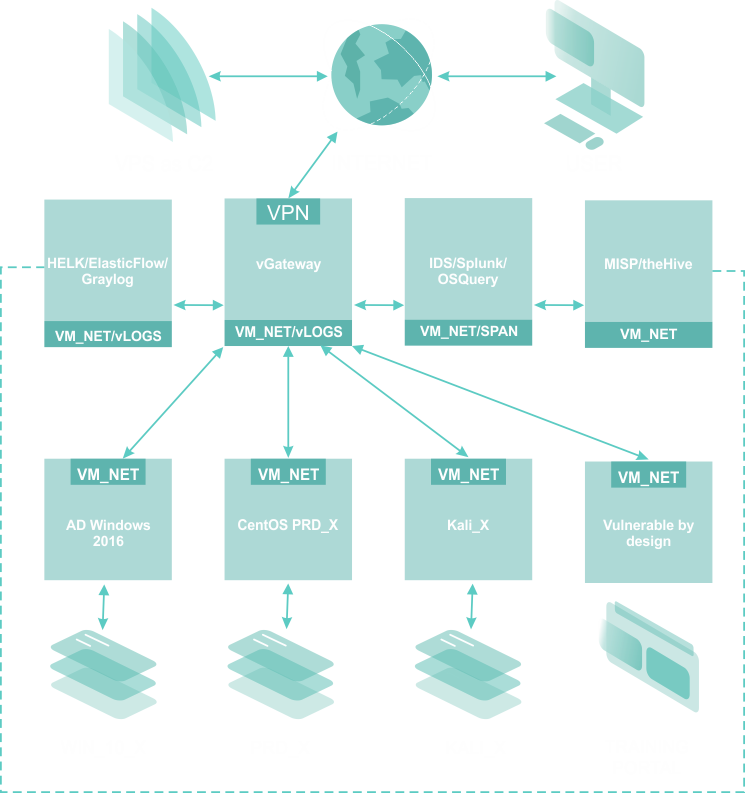
PurpleLABS is a dedicated virtual infrastructure for conducting detection and analysis of attackers' behavior in terms of used techniques, tactics, procedures, and offensive tools. The environment has been created to serve the constant improvement of competences in the field of threat hunting (threat hunting) and learning about current trends of offensive actions (red teaming) vs direct detection (blue teaming).
The primary goal of PurpleLABS is to show and teach you how to generate offensive attack events/symptoms that you will detect in the next phase by using Open Source SOC stack powered by Sigma Rules - the open standard event description ruleset - and the rest of the dedicated, Open Source security solutions in use.
Find how to use the greatest Open Source projects for your Security Operation Center by playing on the real network with Wazuh, Graylog, Elastic Security, Falco, Tracee, Kunai, Sysmon4Linux, FleetDM OSQuery, Syslog, Velociraptor, Zeek, Suricata and more.
Dedicated virtual infrastructure for conducting detection and analysis of modern adversary's tactics, techniques, and procedures.
Analytical interfaces for all-important host, network and application data sources useful during DFIR activities.
Allows for learning about current trends of offensive actions (red-teaming) vs detection points (blue-teaming).
Provides an alternative approach to dealing wich cyber-attacks by pro-active searching across security data in a standardized approach.
Elastic Security unifies SIEM, endpoint security, and cloud security on an open platform, arming SecOps teams to protect, detect, and respond at scale.
Splunk is a software for searching, monitoring, and analyzing data. It captures, indexes, and correlates real-time data and can generate graphs, reports, alerts, dashboards, and visualizations.
Moloch/Arkime is a large scale indexed packet capture and search system. It stores and indexes network traffic in PCAP format, providing fast access to data over ES.
Wazuh is an Open Source Security HIDS Platform. It helps you to gain deeper security visibility into your infrastructure by monitoring hosts at an operating system and application level.
Graylog is a free and open source log management that allows for collecting, indexing, and analyzing both structured and unstructured data from almost any source.
FleetDM is an open source fork of the Kolide Fleet server. This central management server allows you to deploy and control your OSquery endpoints at scale for Hunting, Detection and Incident Response.
Velociraptor is a tool for collecting host based state information using Velocidex Query Language (VQL) queries. It's a unique, advanced open-source endpoint monitoring, digital forensic and cyber response platform.
Sandfly is an agentless intrusion detection and incident response platform for Linux. It automates searching for hackers, malware, and suspicious activity on your Linux systems.
















If you have any question, please use the form below:
This website uses cookies. To find out more, read our Cookies policy. By continuing to use the site, you consent to our use of cookies.