SOC skills development
Develop the team's analytical skills required to work in the Security Operation Center environment.
Learn how the PurpleLABS may boost technical skills on each level of your Security Operation Center Team.
PurpleLABS
The core of PurpleLABS is a dedicated virtual detection/forensics infrastructure that guarantees full visibility across many critical security data sources. By default, it has been powered by a combination of different adversary simulation hands-on exercises that include advanced enumeration, network exfiltration, post-exploitation, and lateral movement scenarios. You can use PurpleLABS as custom, advanced R&D environment for your own network security research needs or as a part of "Attack vs Detection as code" cybersecurity polygon where you will study labs that we have carefully prepared for you. PurpleLabs Cyber Range is fully compatible with EDRmetry Playbook and the content of Linux Attack, Detection and Live Forensics course.
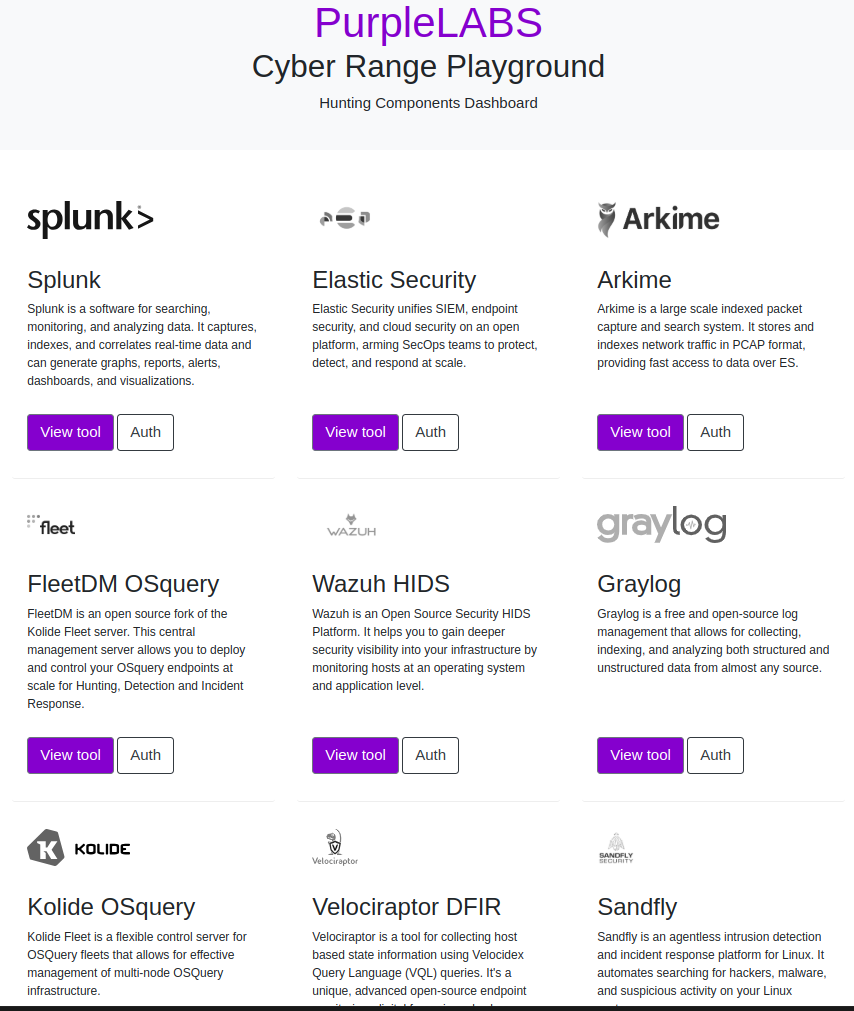
Hunting friendly environment allows you to easily get on the right track to find even the most sophisticated symptoms of chained tactics, techniques, and procedures of modern attackers.
Simple VPN-based access, feeling of real IT environment and usage of exactly the same tools as during real security operations guarantees the fastest way to become a cyber security leader.
Offensive Labs scenarios allow you to generate real traffic of all phases of sophisticated attacks, including C2 channels, data exfiltration, tunneling, and pivoting between critical network segments.
Find and close the gaps in your network security posture before the attacker. Most of the lab scenarios are mapped to industry-standard MITRE ATT&CK® Framework and Sigma rules.
Cost-effective virtual infrastructure hosted in the cloud eliminates the need to install and maintain physical servers, set up tools, network dependencies, privileges and DevOps operations.
A dedicated CTF-style dashboard with a history of completed lab scenarios allows you to measure and track the learning progress of your SOC team and find blind spots in the current level of knowledge.
Minimum theory, maximum hands-on labs only. High-tech Open Source Security workshop with the unique formula of "Attack vs Detection”. Feel the power of the Purple Team and learn what the threat hunting is.
Provided by the highest level professionals in the market. Recommended by big players to expand your Network Security skills and knowledge by focusing on Open Source Security Software.
Extremely deep-dive into Open Source based infrastructure security with a focus on Linux operating systems. Based on 20 years of broad experience.
Develop the team's analytical skills required to work in the Security Operation Center environment.
Increase awareness of the complexity and dependencies between the elements of the APT campaign and the areas of detection.
Acquire Attack Paths, Attack Lifecycles and Security Event Chains skills by combining attacker’s techniques, tactics and procedures (Chain Attack Scenarios).
Understand the value of the Assume Breach approach and simulation of threats after early access (C2, post-exploitation, Lateral Movement, Persistence, Evasion).
Understand what threat hunting is and why it is important. Feel the power of data sources you have and learn how to distinguish between normal vs malicious behaviors.
Acquire skills related to generating suspicious events on the layer of network and Windows and Linux operating systems and methods of their detection.
Understand the potential of Sigma rules and their values for SIEM solutions.
Run a validation of the current security status of the organization's network and the risks involved.
Obtain knowledge on supplying / creating a complete SOC environment using Open Source software.
This website uses cookies. To find out more, read our Cookies policy. By continuing to use the site, you consent to our use of cookies.