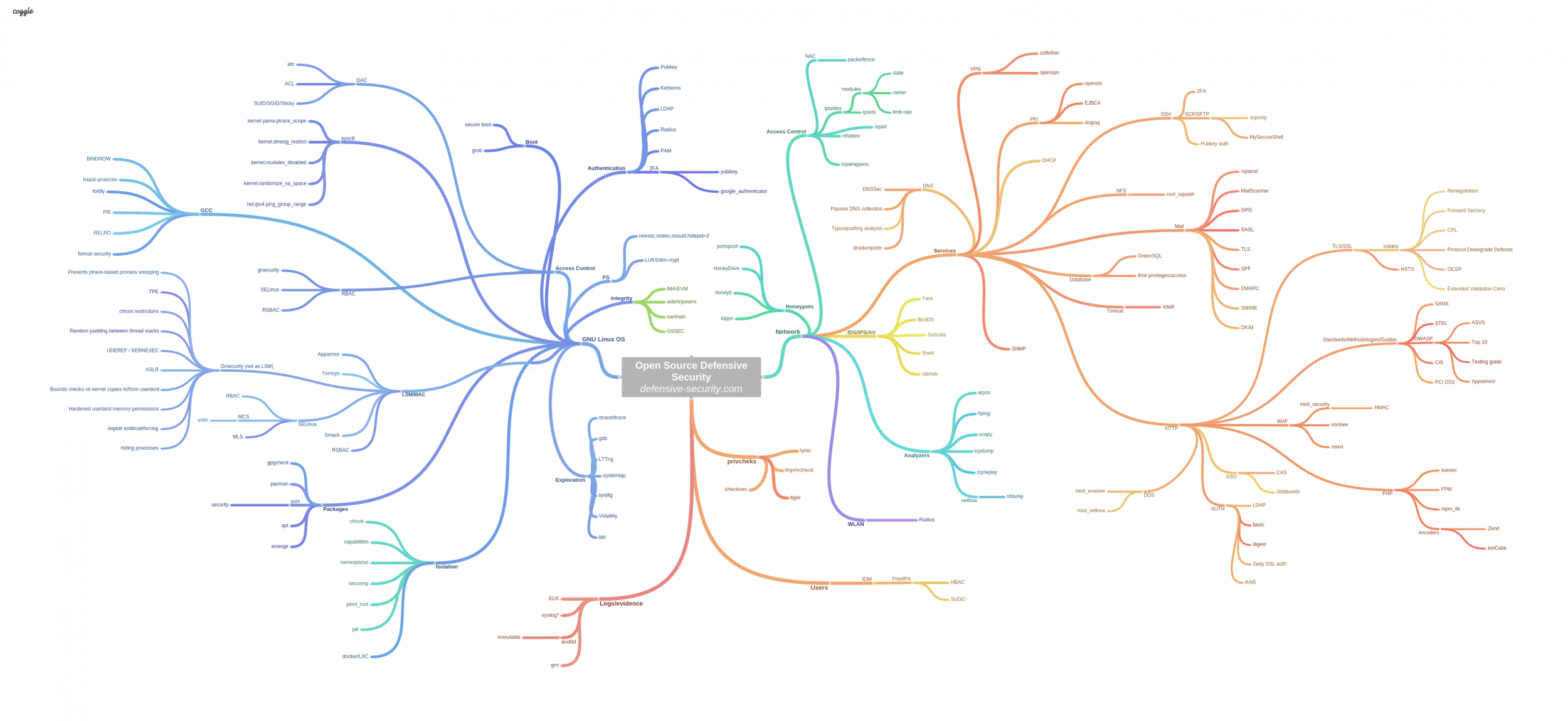
The Map of Linux/Open Source based Hardened Infrastructure.
We *defenders/administrators/*ops/architects also should do our duties in this way! We should definitely start doing our job more precisly, reliable and with more attention to details, because the devil is in details. Simple old-schooled Linux hardening with suid bits erased is no more a case.
Today, correct protection against network and system level exploitation depends on:
- how many protection layers you actually deployed for your core instances.
- how well your systems are configured, hardened, isolated and manag,
- how well your network traffic is monitored and analyzed as well as low level service's syscall lifecycle,
- and a lot more...